Posted:
DNS Done My Way, 2022 Version
Long before NFT existed, we had other digital dreams - domain names! I have quite a bunch of them, still. A few times per year I look at them, think of all the plans I had with them. But I keep them. For nostalgia? Who knows. But managing all of these domains is quite a hassle, especially in 2022, where you can’t simply have an A entry and be done with it.
That’s why I started thinking - can I abstract as many things away, leaving me with an absolute minimum set of dns entries that ideally are identical across all domains? I’ve been working on that this weekend. And I want to share my current setup, so that hopefully others can learn a bit. And maybe some friendly virtual neighbour with more experience can take a look and offer genuine advice to make it even better.
(And that friendly advice came in within minutes after publishing this blog. I have added a new paragraph on CAA :)
Alright, enough talk. Here’s the default config I have deployed on 17 of my domains. The other 6 need special care, as they have legacy websites running on them or other specialties.
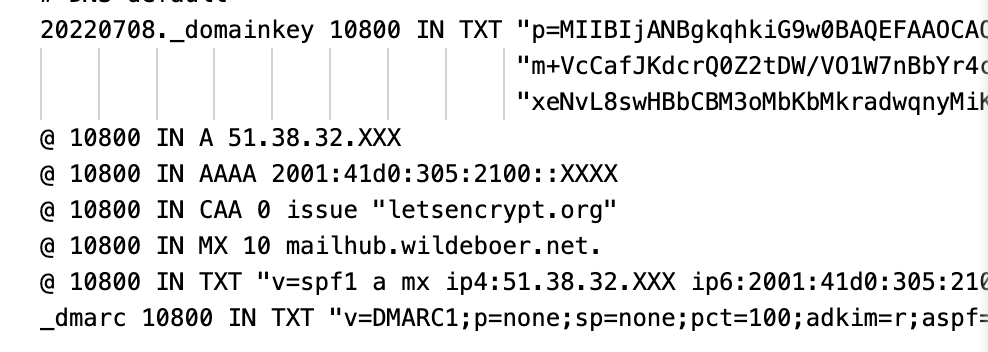 The default zonefile
The default zonefile
I’ll go through each line and explain my logic for why it is the way it is and what it does.
DKIM (Domain Keys Identified Mail)
DKIM is helpful to give your emails a slightly better chance of not being considered spam. You can find out more about what it does and the philosophy behind it at the DKIM Wikipedia page. Suffice to say - you need a cryptographic key in dns so that your DKIM signature, generated by your mailserver, can be verfied.
20220708._domainkey 10800 IN TXT "p=MIIBIjANBgkqhkiG9w0BAQEFAAO...
The 20220708 is the so-called “selector”. One should replace the key file a few times per year, and when I create a new one, I give it the date of creation as filename, so I just need to switch this to the new date and done. Easy.
Now the nice thing is - you can use the same key for many domains. You should have one key per domain, but it is absolutely OK to “recycle” the same key for all your domains - which I do. With this line. I’ve tested it and could find no real problems with this setup. So. DKIM done (dns wise. I won’t bore you with the postfix setup I created for this to work).
Checked with the DKIM Checker - all is good for all my domains.
A and AAAA entries
The next two lines make the domain ping-able (and yes, you can find the real address with a little nslookup or dig, I know ;)
@ 10800 IN A 51.38.32.XXX
@ 10800 IN AAAA 2001:41d0:305:2100::XXXX
I have a little VPS server running (ofcourse) Linux that can be reached both with IPv4 and IPv6. So I let all domains point to those addresses. Maybe I’ll add some sort of generic web landing page on that machine, but for the moment, having a correct A and AAAA is sufficient to me.
CAA Certification Authority Authorization
As was mentioned by Pascal Ernster over on Twitter, a CAA record is definitely a good thing to have by default. This entry informs Certification Authorities which of them I accept to issue certificates for my domain.
@ 10800 IN CAA 0 issue "letsencrypt.org"
Which is an obvious choice for me and my domains - Let’s Encrypt. I do use their service quite frequently, so this is a no-brainer to add to the zonefile.
Checked with the CAA Checker - all is good for all my domains.
mx - let the mails flow
The next line will cause some comments, I know.
@ 10800 IN MX 10 mailhub.wildeboer.net.
I could write a whole series about the pitfalls and little things needed to get a postfixand dovecotcombination working with certbot etc - suffice to say, my mailserver happily accepts and sends mails for all domains. And yes, I know, you really should have more than one mx for redundancy. I really know it. I accept the risks, let’s leave it at that. It has worked for the past 9 years, so I am not too worried about that.
Checked with the mx Checker - all is good for all my domains.
SPF (Sender Policy Framework)
A long, long time ago, when SPF was introduced, I worked at a hosting company where we managed the emails for around 40000 domains. I was tasked to write a web-based SPF generator, which at the time was one of the very first working solutions. So I still know a bit about how to configure this line.
@ 10800 IN TXT "v=spf1 a mx ip4:51.38.32.100 ip6:2001:41d0:305:2100::548c -all"
I hear you already. Yes, a simpler a mx -all would be sufficient. But as I tend to mess up stuff quite frequently, I added the IP addressses too, just to be safe. Again, I have used this config for many years and it never caused problems.
Checked with the SPF Checker - all is good for all my domains.
DMARC (Domain-based Message Authentication, Reporting and Conformance)
The newest thing added. I’ll be honest. I know how it works and how to set it up, but that’s about it. As far as I understand, DMARC is considered to be there, so here it is. I might shorten the entry down after a while, but it is in there and it works.
_dmarc 10800 IN TXT "v=DMARC1;p=none;sp=none;pct=100;adkim=r;aspf=r;rua=mailto:postmaster@wildeboer.net;ruf=mailto:postmaster@wildeboer.net;ri=86400;fo=1"
As you can see, it contains URIs to my postmaster email address at wildeboer.net. Which is in a different domain. So I also had to add an entry for my wildeboer.net domain that allows the setup to work as intended:
*._report._dmarc 10800 IN TXT "v=DMARC1"
This ensures that for any domain that uses the email address postmaster at wildeboer, the DMARC checks succeed.
Checked with the DMARC Checker - all is good for all my domains.
Done
I manage my dns with Gandi.net since many, many years. And they have this nifty feature of a “linked zone” for dns:
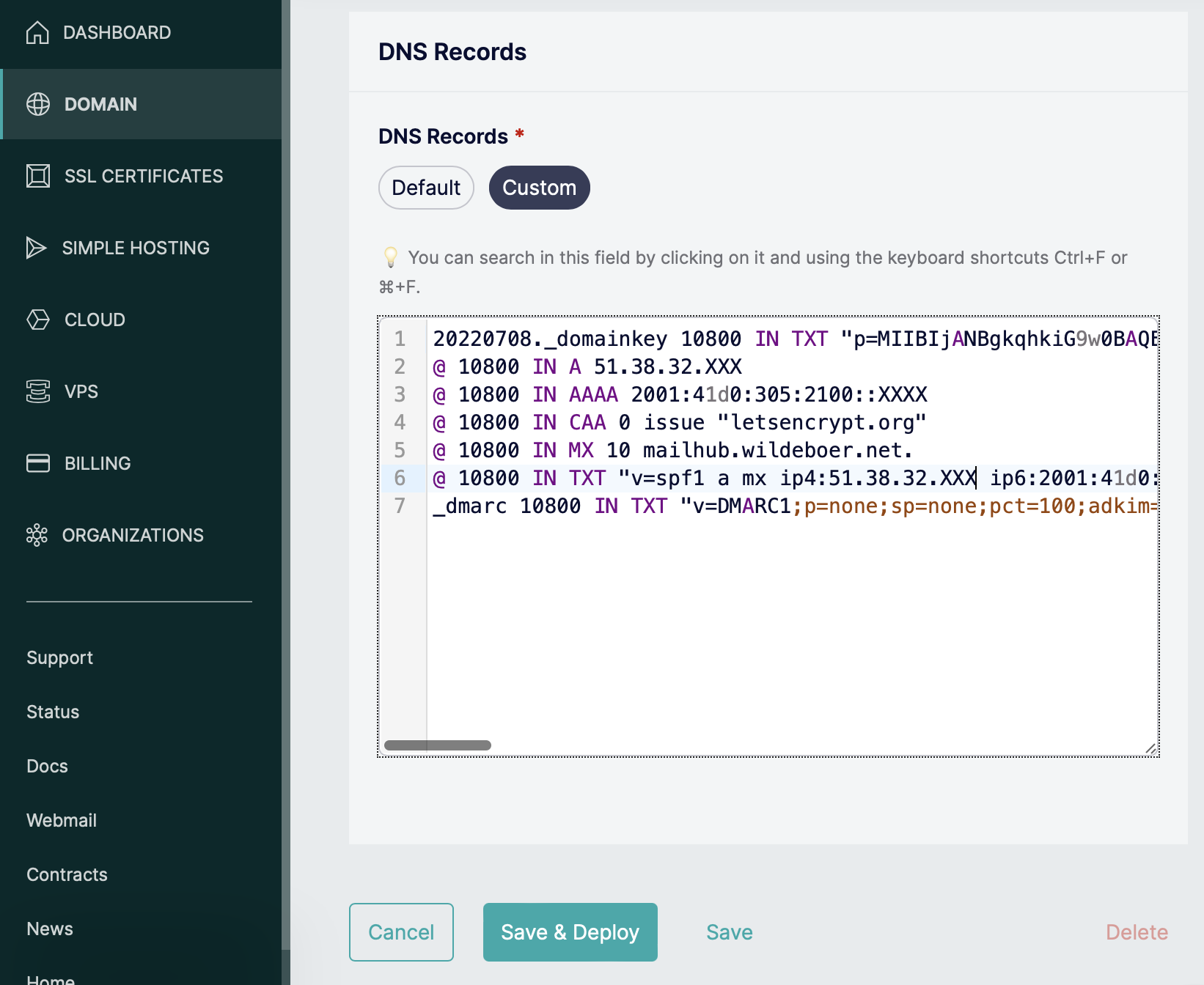 Linked Zone user interface
Linked Zone user interface
And exactly there is where this zone file lives. With a few clicks I can deploy to as many domains I want. So now, when I buy a new domain, I have a working setup in a matter of seconds. This really saves me a lot of headaches. I hope you like it!
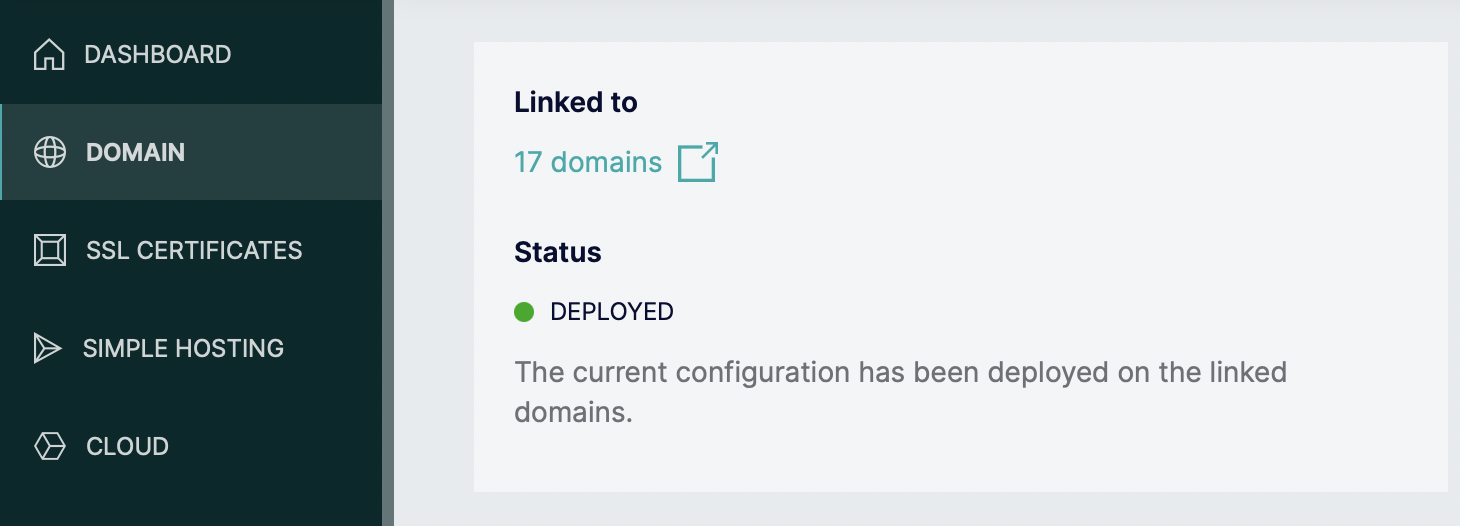 Linked Zone for 17 domains ATM
Linked Zone for 17 domains ATM
I am looking forward to your suggestions on how to make it better. I am not perfect nor a real dns guru. This is my “good enough” solution that works for me and my domains. And it was fun to plan and deploy!


COMMENTS
You can use your Mastodon or other ActivityPub account to comment on this article by replying to the associated post.